Android malware evolution
The evolution of Android malware may be anticipated to be quite similar to desktop malware initially. However, Android’s great market share as well as its openness and its unique security features have all provided an interesting opportunity for the attackers. In addition, smartphones have introduced new technologies that can lead to more diverse and bigger attack vectors. For instance, mobile cellular data, high-quality cameras and sensors and location-aware services are appealing launching points for attackers. All these reasons have made Android malware evolve faster over time.
In this post, readers are provided with an evolution timeline of Android malware (Fig. 1) and some relevant information specific to each year gathered from security threat reports of popular cyber security firms, including F-Secure (Finish company), Kaspersky Lab (Russian company), McAfee (American company), Symantec (American Company), Trend Micro (Japanese company), and, finally, Avira (German company).
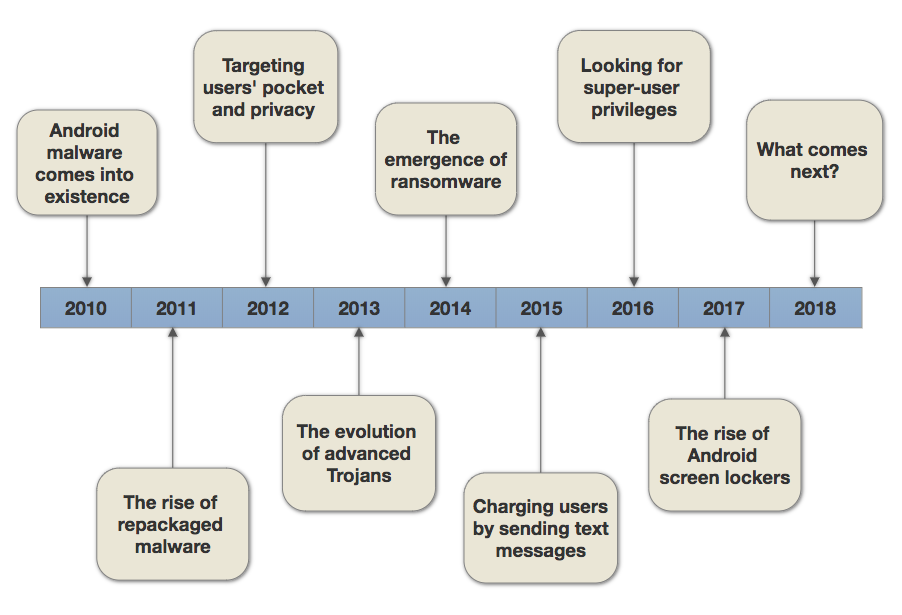
2010 - Android Malware Comes into Existence
The first malware in Android operating system was first detected in August 2010. This Trojan family, known as FakePlayer, pretended to be a media player for watching porn video clips in Android. However, it was just an app that sent SMS text messages (with 798657 as body) to premium-rate numbers (in this case, 3353 and 3354 numbers) without user’s consent (Listing 1). It had an icon in its res directory which looked very similar to the legitimate Windows Media Player application.
.line 35
invoke-static {}, Landroid/telephony/SmsManager;->getDefault()Landroid/telephony/SmsManager;
move-result-object v0
.line 54
.local v0, "m":Landroid/telephony/SmsManager;
const-string v1, "3353"
.line 55
.local v1, "destination":Ljava/lang/String;
const-string v3, "798657"
.line 57
.local v3, "text":Ljava/lang/String;
const/4 v2, 0x0
const/4 v4, 0x0
const/4 v5, 0x0FakePlayer was an easy-to-analyze malware family with only 3 main classes and almost 350 lines of code. It was specifically developed to target Russian smartphone users for two main reasons. First, Android official market (known as Android Market in 2010) was not accessible world-wide, and, second, money could be sent easily on Eastern European telecom carriers.
Later on, cyber security companies discovered the first spyware in Android malware, called Tapsnake. Tapsnake was a Trojan embedded into a game (Tap Snake) capable of leaking location information to a remote server every 15 minutes. It could also allow a third-party to track user’s geographical location by installing another paid app, called GPS Spy. Two key registration information, including an email address and a key were required to be typed in both Tapsnake and GPS Spy to enable geo-location tracking. These information were acquired by social engineering techniques.
Geinimi was another newsworthy Android malware family initially detected by Lookout at the end of 2010. This family was the most sophisticated malware found by that time with innovative capabilities. Firstly, it was a repackaged version of legitimate Android apps like President vs. Aliens (an educational app) and Baseball Superstars 2010 (a game app) to name a few. Secondly, it made use of two anti-analysis techniques to hide its malicious behavior, including network communication encryption and network communication code obfuscation. Thirdly, it had some botnet-like capabilities with more than 20 commands implemented in its source code. Since then, Geinimi has been found in a wide range of locations, ranging from unofficial marketplaces to official ones.
2011 - The Rise of Repackaged Malware
Malicious apps increased in number from 84 samples in 2010 to more than 1000 in 2011. Also, inspired by the success of Geinimi in 2010, repackaging benign apps was rapidly imitated by malicious apps from several new families such as ADRD, Pjapps, DroidDream, DroidDreamLight, Zsone, BaseBridge, DroidKungFu, jSMSHider, GoldDream and AnserverBot in 2011. In total, around 86% of malware specimens found in 2010 and 2011 were repackaged versions of legitimate apps.
ADRD and Pjapps were the first Trojan families detected in February 2011. Both of these families could steal sensitive device information, including International Mobile Equipment Identity (IMEI), International Mobile Subscriber Identity (IMSI), device ID, line number, subscriber ID and SIM serial number once special conditions were met. Later, they sent this information to remote servers. These types of malware are commonly known as Logic Bomb Trojans. ADRD could be activated once the operating system started, the network connectivity changed or whenever the device received a phone call. However, Pjapps only started execution when the device signal changed. In addition to stealing capability, ADRD family could change the device settings to enable/disable data connectivity in order to send or receive information all of which would result in high data usage. Also, Pjapps was able to send text messages, install a new application and to add a browser bookmark.
DroidDream and DroidDreamLight were the next family of malware discovered one and three years later which repackaged legitimate Android applications to compromise the target device. Similar to the earlier detected families in this year, they could steal sensitive information, including IMEI, IMSI, device model, device language and country and leak them to remote servers. DroidDreamLight could even steal information from text messages, contact lists, call logs and Google account credentials. The main difference between these two families was in the way they behaved in the infected device. DroidDream tried to get root privileges at the first step, after which It was able to manipulate the device settings, system files and SD card. On the contrary, DroidDreamLight ran in the background silently and leaked the sensitive information which were stored encrypted in a configuration file.
Zsone was another malware family found exactly at the same month as DroidDreamLight though with quite different characteristics. This Trojan was developed to target Chinese users mainly. Once installed on the device, it could send text messages to premium-rate numbers related to subscription for SMS-based services to charge the user. It also kept a record of its sending status in an XML file. Incoming text messages from certain numbers could also be intercepted by this family.
BaseBridge and DroidKungFu - both with several variants and stealing capabilities - were the next families of Android malware detected in 2011. Additionally, similar to DroidDream family, they first attempted to gain root privileges in the target device. Once successful, they stole a variety of information, including IMEI, device model and manufacturer and OS version and sent them to remote servers. BaseBridge was also capable of sending/removing text messages, dialing phone numbers and monitoring phone usage. On the other hand, DroidKungFu could install/remove any packages and modify the homepage of web browser without user’s consent.
jSMSHider was the second malware family with big differences in behavior comparing with the earlier discovered families. It was a Trojan which affected smartphones with a customized ROM. It could exploit a vulnerability in these devices and install a payload onto the ROM to communicate with a remote server and receive operational commands. It was then able to read, send and remove text messages (to hide its malicious intent), install apps on ROMs, perform a silent install or update of the APK and download an application from a URL.
Detected after jSMSHider, GoldDream was another logic bomb Trojan with versatile stealing capabilities. It could record the date, time, message body and the senders of text messages upon receiving messages. It could also store the date, time and phone number once any calls were made or received. In addition, it was able to make phone calls, send text messages and install packages without user’s knowledge. Device ID, SIM serial number and Subscriber ID were among the most important sensitive information this malware family could steal from the compromised device.
AnserverBot was the third family with different behavior in contrast to its predecessors. It first tried to lure the device user by showing fake upgrade dialog boxes for the host app. It then installed the first payload that could run silently in the background. Afterwards, a second payload could be loaded and executed dynamically either by the host app or the first payload. Finally, it could connect to the remote server to take the commands. This family was one of the pioneers in using anti-analysis techniques as well. First of all, most of the code in both payloads were obfuscated. Second, AnserverBot had a mechanism to avoid the infected application from being repackaged again. Last but not least, it could detect the existence of three smartphone anti-virus software.
2012 - Targeting User’s Pocket and Privacy
Similar to previous years, Android was by far the most commonly targeted smartphone operating system in 2012, constituting 95% of unique threats. These threats were found mostly in Eastern Europe and Asia though the number of threats in the rest of Europe and the United States had increased from the previous year. This year witnessed 350,000 malicious and high-risk Android apps comparing with less than 1300 malware in 2011. Also, they had an increase in the sophistication level. Furthermore, 103 Android mobile malware families were discovered in 2012.
While stealing users’ sensitive information - known as privacy leakage - was still among the main goals of malware authors, the primary focus changed significantly in this year. In particular, developing premium service abusers and adware outnumbered other types of Android malware. In general, 48.58% and 38.30% of detected Android malware in 2012 were service abusers and adware.
Commonly disguised as popular legitimate apps, premium service abusers were designed to convince users to install them at the first step. Later, they could charge smartphone user by sending text messages to premium-rate numbers. Moreover, special variants could download other malicious apps, and, also, steal information from infected devices. For instance, variants of FakeInst and SMSBoxer families spoofed several popular Android games and social networking apps, including "Bad Piggies", "Angry Birds Space" and Instagram. Also, Gappusin variants downloaded other malicious apps and stole information from compromised devices.
Aggressive adware - ranked as the second popular types of malware in 2012 - could also disclose user’s or device’s sensitive data to third-parties by continuously showing advertisements to the smartphone user. These malware posed a high privacy risk to users and could gain big profits by selling users’ information to untrusted parties. For instance, variants of Plankton family were able to collect personal information such as email addresses and phone numbers, and, could later, forward them to several third parties.
2013 - The Evolution of Advanced Trojans
While premium service abusers and adware remained the most common Android threats in 2013, four important changes happened all of which affected the Android malware evolution. First of all, the number of smartphone users grew in 2013 most of which were less aware of security risks of Android apps. Second, Google’s official app store, known as Google Play Store (introduced in 2012), superseded Apple’s App Store and could become the largest smartphone app market at that time. This increase in popularity was later abused by malware authors. Third, an important vulnerability, called "Master Key", was found in July 2013 that allowed installed apps to be turned into malicious without user’s consent nor knowledge. Last but not least, several toolkits started to be sold for trojanizing Android apps in underground markets.
Android continued to be the most targeted smartphone operating system in this year. F-Secure and Trend Mircro reported 358 new Android malware families and 1 million new Android threats in 2013 alone. On the other side, malware authors put their focus on popular applications in online stores, especially games and social networking apps, to maximize the number of victims. Thus, trojanized versions of popular apps made up most of the additions to 2013’s list of Android malware families. In particular, advanced Trojans, adware and rogue security apps were among special interests of malware developers. Furthermore, spreading malware through email and fake websites were used commonly.
Among Trojans detected in 2013, Stels, Obad, Dandro, Fakeguard, Fakedefender and Pincer were the most popular ones. Stels was developed mainly to target smartphone users in Russia. Initially detected in 2012, F-Secure identified over 1,300 unique Stels samples that could be divided into three major variants as of 2013. It was the first Android malware distributed via spam e-mails, and a bot that used Twitter to update its C&C server addresses. Also, it was one of the pioneers developed to target multiple platforms (Android and Windows). Stels could act as a banking trojan and intercept incoming text messages to steal mobile Transaction Authentication Numbers (mTANs), thus defeating the two-factor authentication method used to validate an online banking transactions. In addition, it could leak sensitive device information, including IMEI and IMSI.
The second common Trojan, Obad, could exploit “Master Key” vulnerability to elevate its privileges at the first step. Once exploited, malware developers were able to embed their malicious codes into the modified apps. An interesting point was that malware developed this way resembled legitimate applications in terms of their signatures.
Discovery of Obad Trojan revealed that mobile threat landscape had evolved a lot since 2012 and that attackers had found new methods to compromise devices. For instance, Dandro was a Trojan developed using a toolkit, called binder, which was available for developing Remote Access Trojans (RATs). This malware began to circulate using email attachments with which the remote attacker was able to perform a wide variety of operations, including sending and retrieving text messages, retrieving contacts and call logs, acquiring the device location and using its camera to name a few. Later, a variant of Fakeguard family was detected which was a repackaged version of a legitimate Korean app. Once installed on the device, the app attempted to download its malicious code through sending update notifications to users. Fakedefender was another advanced Trojan and the first Android malware that came into existence by leveraging security apps on smartphones. This rogue security app tried to persuade users into paying a considerable amount of money to get rid of all non-existent (or fake) threats from their device. Finally, variants of Pincer and FakeKRBank were found that stole text messages containing TANs similar to Stels and were developed mainly to target users of the Commonwealth Bank.
2014 - The Emergence of Ransomware
Cybersecurity firms observed interesting changes in Android malware during 2014. On the one hand, the number of variants per family dropped by 16%. In 2012, 38 new Android variants per family was detected. This number increased to 57 per family in 2013, and it decreased again to 48 in 2014. One the other hand, 17% and 36% of Android apps were found to be either malware in disguise or grayware. While not malicious by design, Android grayware could annoy users by doing unintentional activities such as tracking user’s behavior.
This year was undoubtedly the first time where different types of Android ransomware and bitcoin-mining malware were discovered. At this period, cybercriminals looked at developing ransomware as a lucrative business, and bitcoins became the payment method of choice by most new ransomware because of its strong anonymity. In particular, some ransomware got the press, including Koler, Slocker, Simplelocker, CryptoLocker, CryptoDefense and CryptoWall.
Koler was almost the first discovered Android ransomware. It was the mobile extension of "police-themed" Reveton ransonware. This app was assumed to offer access to adult contents. However, once installed on the device, it started to send notifications to scare the user into paying a fine for supposed illegal activity. Koler did not encrypt any files despite its claims; it only disabled the Back button to keep the ransom demand prominent.
Slocker - the first Tor-encrypted ransomware - could disable the Back button as well. However, it had much more capabilities. For instance, variants of Slocker were able to encrypt images, document and video files as well as communicating with a remote server via Tor network or SMS messages. Simplelocker was a similar ransomware detected in June 2014 with file encryption capabilities. It employed an FBI social engineering theme like the famous Porndroid ransomware to deceive users. However, Porndroid could take the victim’s picture to display it later alongside the ransom demand. Later on, other ransomware were also spotted which made use of a Tor component such as Torbot, Dendroid, CryptoLocker, CryptoDefense and CryptoWall.
Despite developing these advanced Android ransomware, malware developers began to explore other ways through which they could extort money. Soon after that, they started to target Network-Attached Storage (NAS) devices, where large quantities of files were stored. For instance, Synolocker was developed to target Synology NAS devices by using a previously unknown vulnerability in Synology’s DiskStation manager software. Once found its way into the device, it could encrypt all files, holding them for ransom.
In addition to developing different types of ransomware, campaigns had special attention to bitcoin-mining malware as well. As an example, Kagecoin could start mining for bitcoins on Android devices as soon as it was installed. This allowed cybercriminals to use infected mobile devices’ computing resources to mine for bitcoins and other cryptocurrencies. Furthermore, infection resulted in shorter battery life, which could ultimately lead to a shorter device lifespan.
2015 - Charging Users by Sending Text Messages
While ransomware remained frequent in 2015, sending text messages to premium-rate numbers was the most common behavior observed among the top 10 Android malware families. In particular, SmsSend, Slocker, FakeInst, GinMaster, GingerBreak, SMSpay, DroidRooter, Dialer, SMSKey and Coudw made up 25% of the total amount of Android malware detected in 2015.
SmsSend, FakeInst, SMSpay and SMSKey were popular Trojans that charged users’ phone bills by sending text messages to premium-rate phone numbers or a subscription-based paid service. Also, variants of these families used randomization techniques to evade detection by antivirus products. Throughout this year, France was intensively attacked by SmsSend Trojan family.
In addition to SMS-sending Trojans, Android security flaws were exploited to lunch new attacks against users in 2015. For instance, Android’s MediaServer component took a lot of hits as its vulnerabilities could be exploited to perform attacks using arbitrary code execution. These attacks could force a device’s system to go on endless reboot in order to drain its battery. They could even be used to render Android devices silent and unable to make calls due to unresponsive screens. Other vulnerabilities exploited in this year were related to Android debugger and installer components. A vulnerability in the former component was utilized to expose a device’s memory content, while a hijacking vulnerability in the second component gave hackers the ability to replace legitimate apps with malicious versions in order to steal user’s information.
2016 - Looking for Super-User Privileges
Android vulnerabilities increased by 206% in 2016; however, attacks slowed for the first time since attackers faced security improvements in the Android’s architecture. Specifically, 4 new Android malware families and 3.6K new variants were found in this year. On the other hand, new ways were devised to bypass Android protection mechanisms. For instance, variants of the Tiny SMS Trojan were detected that were able to use their own window to overlay a system message warning users about sending a text message to a premium-rate number.
The year’s most prevalent goal among Android malware was focused on gaining as much privileges as possible on the victims’ devices. This was achieved using one or more than one application.
In order to obtain super-user privileges using one single application, Trojans with almost unlimited capabilities were developed. These Trojans could install other advertising apps or malware stealthily. Representatives of this type of malware had been repeatedly found in the official Google Play app store in 2016 (e.g., Ztorg.ad was a Trojan that pretended to be a guide for Pokémon Go application).
App collusion was a mean to obtain the maximum level of privileges using more than one application. Here, instances of app collusion were discovered in a group of applications that used a particular Android SDK with a wide range of permissions. Co-working together, any of applications participated in the app collusion, could bypass the Android OS limitations and respond to commands from a remote server via the app with highest privileges. This could result in the maximum elevation of privileges and the most capable bot functionality based on all apps that took part in the negotiation.
In addition to the attempts made in gaining super-user privileges, a considerable growth was observed in ransomware. This rise was caused by the active distribution of two families of Android ransomware, including Fusob and Congur. Fusob displayed the ransom demand on top of other windows, thus making it impossible to use the device, while Congur set or reset the device passcode and gave attackers administrator rights to the device.
Malware products and services such as malware kits offered on Dark Web marketplaces boosted the rise of Android malicious apps in 2016 as well. For example, DroidJack was offered by different vendors on four major marketplaces. This popular Remote Access Trojan (RAT) was sold openly on the Clearnet and DarkWeb. The Android bot rent service (BaaS, or Bot as a Service) was also available for purchase. The bot, which was available both in Russian and English, could be used to gather financial information from Android smartphones.
2017 - The Rise of Android Screen Lockers
New mobile malware variants grew by 54% in number in this year comparing with the previous one. However, the act of rooting Android devices decreased as newer versions of Android OS provided increased functionality. Also, the proportion of Android devices not being encrypted fell down for the first time. An analysis of Android smartphones revealed that only 20% of devices were on the latest major release.
Once again, the easy availability of exploit kits and dark web sources boosted the rapid creation of new Android malware. In particular, new ransomware rose by 36% in the second quartile, largely from widespread screen-lockers. Also, this year witnessed serious vulnerabilities exploited to provide attackers with root privileges (e.g., Dirty COW vulnerability exploited by ZNIU malware).
2018 - Android Malware Predictions
Threats to mobile devices will increase significantly in 2018 by the widespread usage of mobile phones for surfing the internet and the growing rate of mobile transactions. However, Android will still be the most popular target platform for attackers because of its high market share. Specifically, more high-end APT malware will be discovered due to an increase in the number of attacks, and, also, improvements in the security technologies.
Security experts believe that advanced types of ransomware such as RaaS will emerge targeting users’ sensitive information. in addition, Android malware will explode on Google Play according to their inspections.
Hijacking cryptocurrencies will likely rise in number as well due to their significant worth at the moment. Therefore, malware writers would try to secretly mine cryptocurrencies without users’ knowledge.